
Softdel signs TECH VEDA for corporate training on Embedded Linux
Softdel signs TECH VEDA for delivering corporate training program on Embedded Linux. Softdel becomes our 49th client.
In this final installment of our series, we synthesize our exploration of diverse Linux boot processes by examining two critical, cross-platform themes: securing the chain of trust and ensuring system resiliency through atomic updates. While the implementations vary, the underlying goals are universal, reflecting the core challenges of building reliable and secure modern computing systems.
A secure boot process establishes a “chain of trust,” where each software stage cryptographically verifies the next before executing it. The implementation of this concept is tailored to the specific threat model of each platform.

A failed update can render a device unusable. To prevent this, modern systems employ atomic update strategies that ensure an update is either fully completed or not at all, always leaving the system in a bootable state.
The Linux boot process is a rich tapestry of specialized adaptations. From the atomic UKIs on modern servers to the multi-stage ascent of embedded SoCs, each platform has forged a unique path from power-on to init. This diversity is a testament to the kernel’s flexibility. As technology evolves, we see a convergence of ideas: the principles of verifiable boot artifacts and transactional, image-based updates are becoming the new standard across all domains, pointing to a future of Linux systems that are simpler to manage, more resilient to failure, and provably secure from the very first instruction.

Softdel signs TECH VEDA for delivering corporate training program on Embedded Linux. Softdel becomes our 49th client.
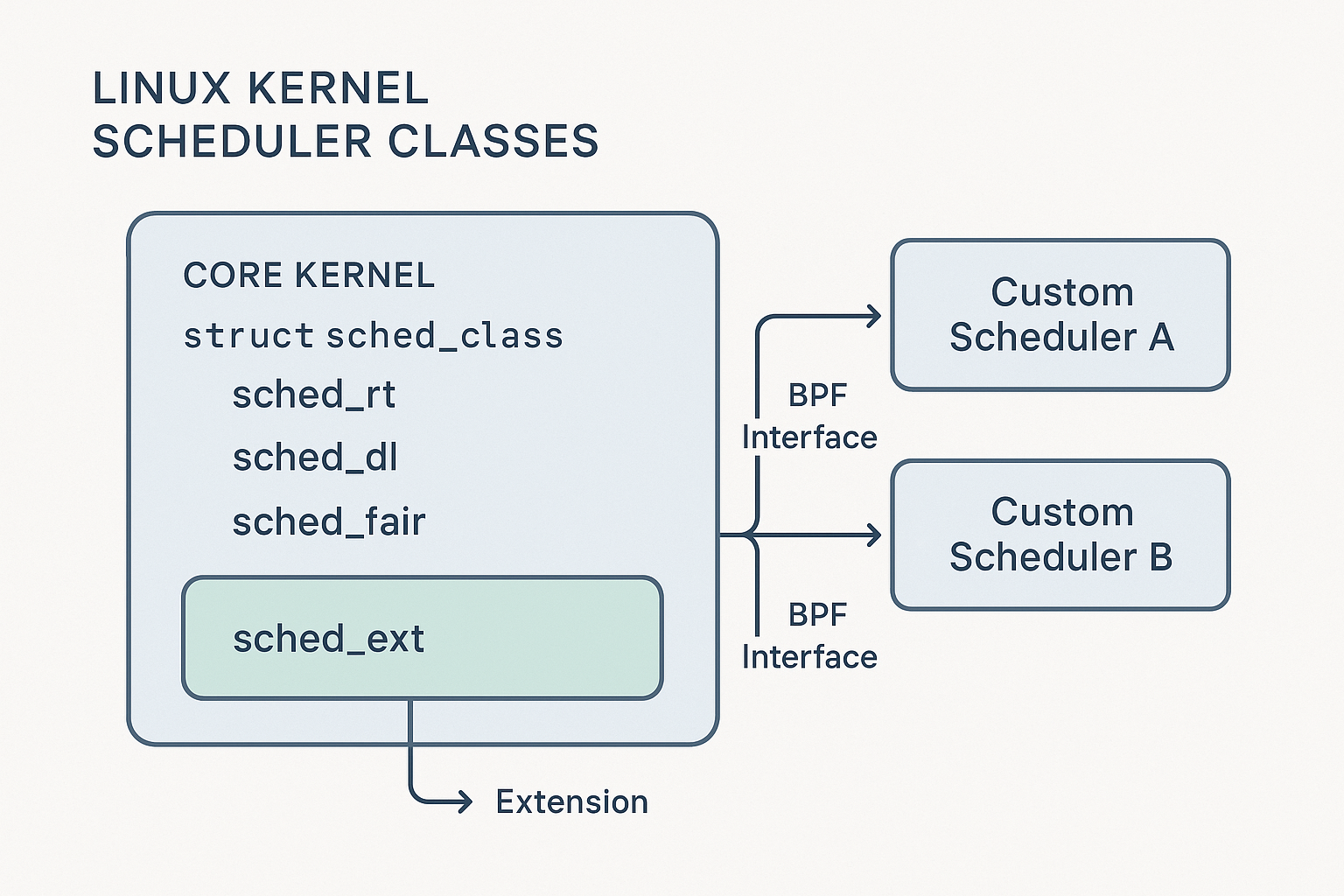
This article provides a deep dive into the major scheduler classes, their unique design goals, and the management utilities powering the system.
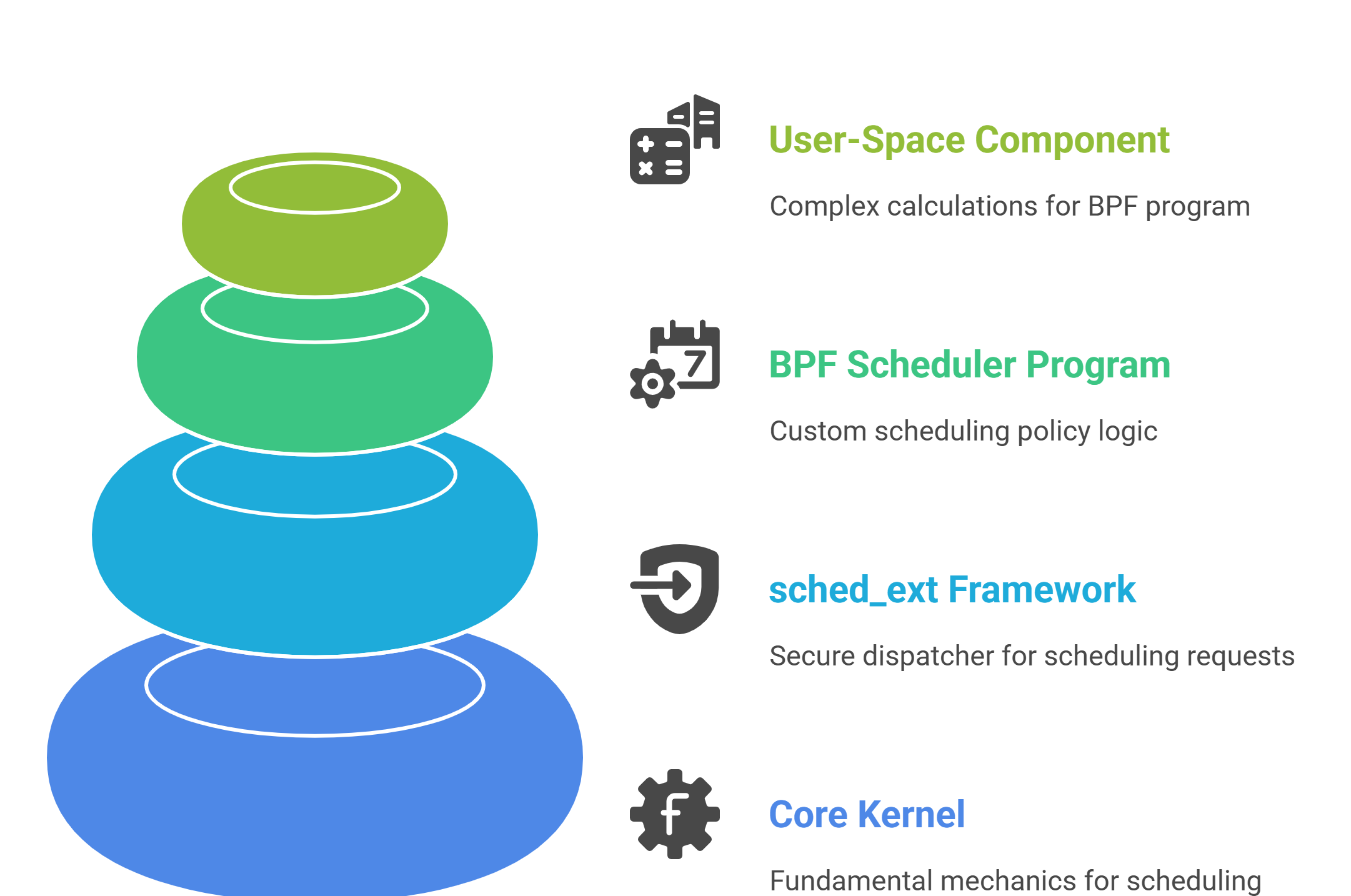
sched_ext is not a scheduler; it’s a framework that securely connects custom BPF programs to the core kernel. Its architecture consists of four distinct layers that separate responsibilities cleanly.
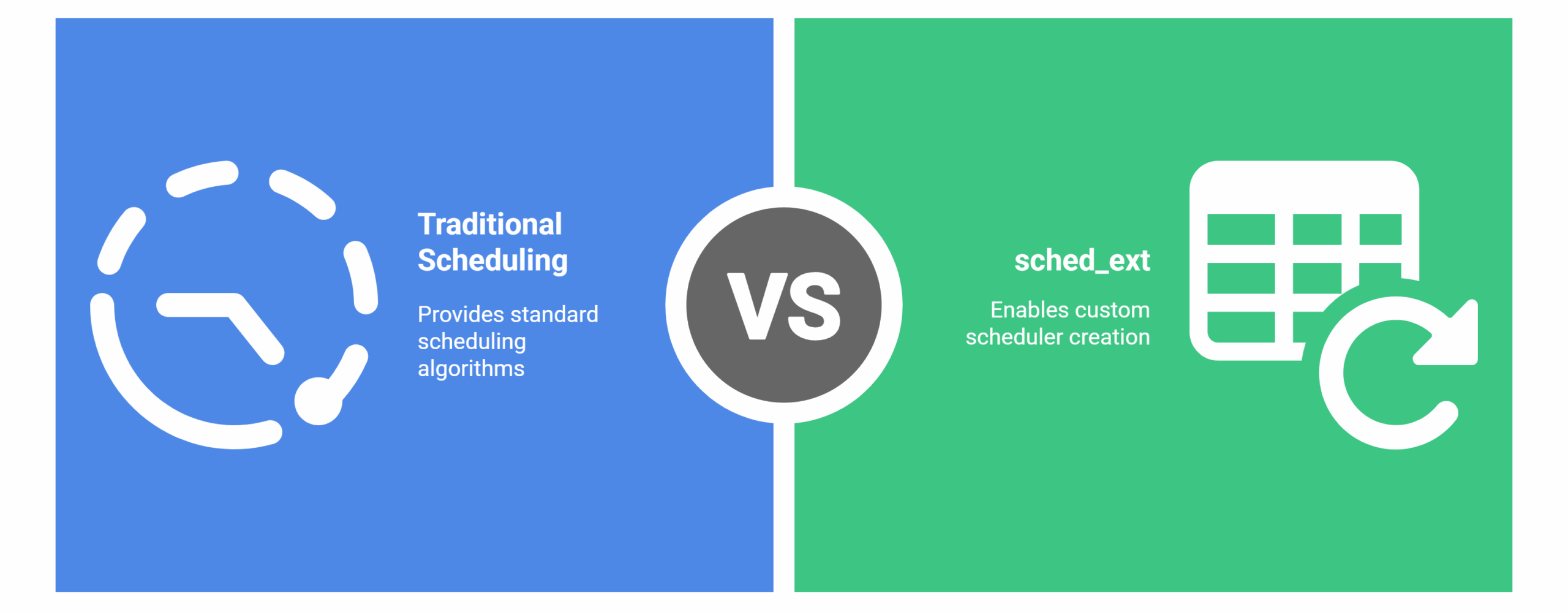
For decades, general-purpose schedulers like CFS and EEVDF, powered everything from phones to supercomputers. But with complex hardware and specialized software, the “one-size-fits-all” scheduling model began to crack. This tension set the stage for sched_ext.